If you are an IT admin and has deployed OneDrive sync app to your clients, this post can help you to sign clients silently using Windows credentials. Basically, if clients have joined Windows 10 to Azure AD, they don’t need to sign in to OneDrive sync app individually. To achieve this, you can silently sign in users to OneDrive sync app with Windows credentials using Group Policy.
When we have deployed such a Group Policy configuration setting, the OneDrive app can automatically use the work or school account client has signed in to Windows 10. This all happens without the user interaction and hence it is known as silent sign in. According to Microsoft, if syncing the user’s entire OneDrive would cause the available space to drop below 1 GB, OneDrive will prompt the user to choose folders to sync. This is also valid if syncing size exceeds the threshold you set, in case if Files On-Demand feature is not enabled.
You can also use this configuration with Windows 10 devices with on-premises environment that uses AD. This is possible with availability of hybrid Azure AD configuration.
So here’s how you can configure that setting and silently sign in users to OneDrive sync app with Windows credentials.
Silently Sign In Users To OneDrive Sync App With Windows Credentials
1. Open GPO Editor by using gpmc.msc command in Windows Server and by running gpedit.msc in Windows client edition.
2. Next, open the GPO Editor window, navigate here:
Computer Configuration > Policies > Administrative Templates > OneDrive
If you don’t have OneDrive listed after Administrative Templates, follow this guide.
Note: Policies folder is not available in client edition.
3. Double click on Silently sign in users to the OneDrive sync app with their Windows credentials policy setting to modify it.
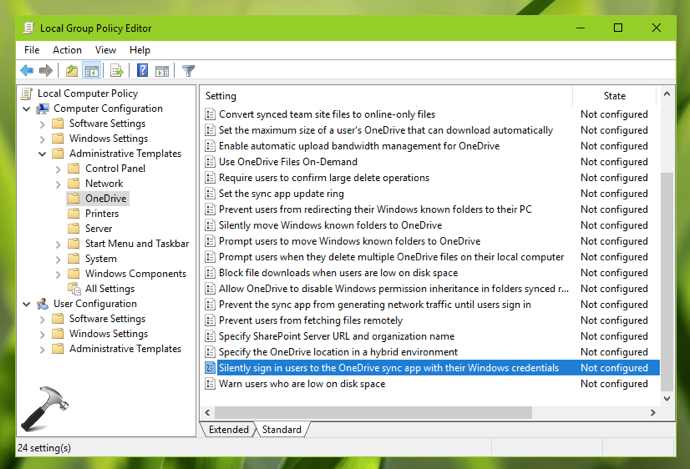
4. Configure the policy setting to Enabled. Close GPO Editor and update the GP engine.

After few moments, the policy should be in effect on client machines.
That’s it!










Leave a Reply